Introduction
- LDAP URL
- Bind user and password
- User search base
- User search filter
LDAP can be configured using UI(v6.1 onwards) or API. One can configure one or more LDAPs at the same time. Once configured, the LDAPs will appear on the login and sign up page as a dropdown.
Configure the LDAP via UI
Super admins can configure LDAP via UI (v6.1 onwards) by going to Extras from the home page.
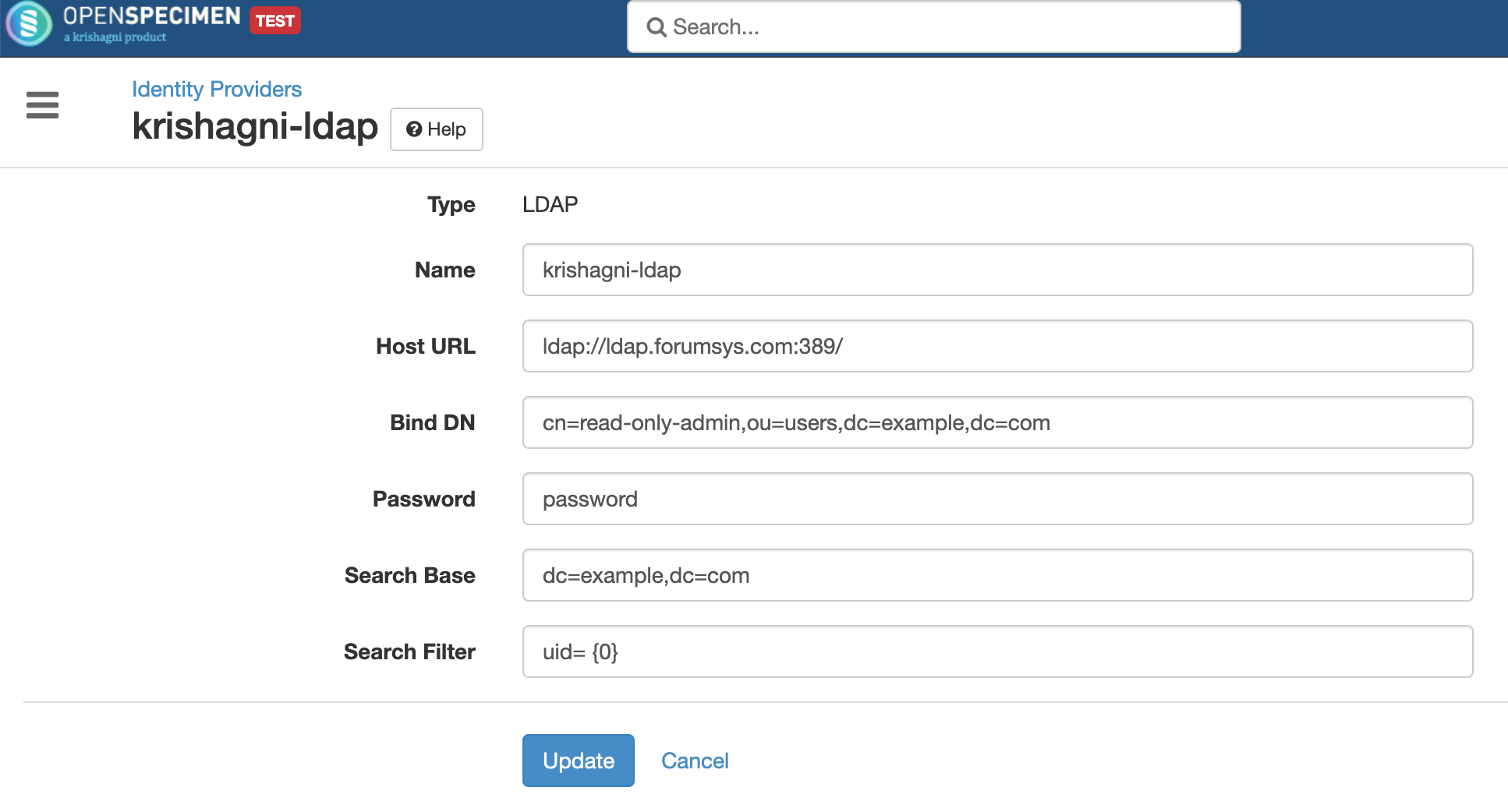
Click on 'Identity Providers' and create a new entry for registering to your LDAP. Select the type as LDAP and fill all required details
Once created, the list of all LDAPs registered are displayed and can be updated if required.
Item | Description | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Host URL | LDAP URLs have this syntax: ldap[s]://<hostname>:<port>
| |||||||||
| Bind DN | This is required for authenticating to the directory. Eg. "cn=read-only-admin,ou=users,dc=example,dc=com" | |||||||||
| Password | Password of the Bind DN user. | |||||||||
| Search Base | User search base, from where the search will be started. It might be an empty string like "" or "ou=People". If Oracle DBMS is used, then an empty string is treated as null, which will fail LDAP authentication. Therefore it is advised to specify the base node from which the search needs to be carried. Eg. Suppose users are resided in following directory:
1. ou=others,dc=example,dc=com
2. ou=users,dc=example,dc=com
3. ou=people,dc-example,dc=com
url - ldap://ldap.forumsys.com:389
SearchFilter - "(uid={0})" or "(sAMAccountName={0})"
SearchBase - ""
Search will start from "dc=example, dc=com", It will search user in all the sub directories.
OR
url - ldap://ldap.forumsys.com:389
SearchFilter - "(uid={0})" or "(sAMAccountName={0})"
SearchBase - "ou=people"
Search will start from "ou=people,dc=example,dc=com". It will search user only in ou=people.
| |||||||||
| Search Filter | Search user using an attribute. Eg. "(uid={0})" or in case of active directory "(sAMAccountName={0})" |
Debugging LDAP Issue
Run the below command on command prompt/terminal and fill the same details as configured on OpenSpecimen UI. This command will give you an error if there is an issue with configuration, and if it works fine, then the same configuration will work in OpenSpecimen.
ldapsearch -x -H <ldap_host> -b "<search_base>" -D "<bind_dn>" -W "objectclass=account"
For Example:
ldapsearch -x -D "cn=Manager,dc=krishagni,dc=in" -H ldap://192.168.121.133 -b "ou=People,dc=krishagni,dc=in" -W "uid=test"
The command will prompt for the password. Enter the same password that you entered in the password field on UI.
Here 'test' is the user account created in LDAP, and the same user needs to be created into OpenSpecimen. Here is a wiki page to setup LDAP users. (refer to via UI section)
Delete the LDAP configuration (via backend)
Note down the domain name and provider id which needs to be deleted.
select * from os_auth_domains;
Delete the entries of the identity provider and their properties from respective tables.
delete from os_auth_domains where domain_name='<identity-provider-name-to-be-deleted>'; delete from os_auth_provider_props where AUTH_PROVIDER_ID = <provider-id-query#1>; delete from os_auth_providers where identifier = <provider-id-query#1>;