Introduction
- LDAP URL
- Bind user and password
- User search base
- User search filter
LDAP can be configured using UI(v6.1 onwards) or API. One can configure one or more LDAPs at the same time. Once configured, the LDAPs will appear on the login and sign up page as a dropdown.
Via UI
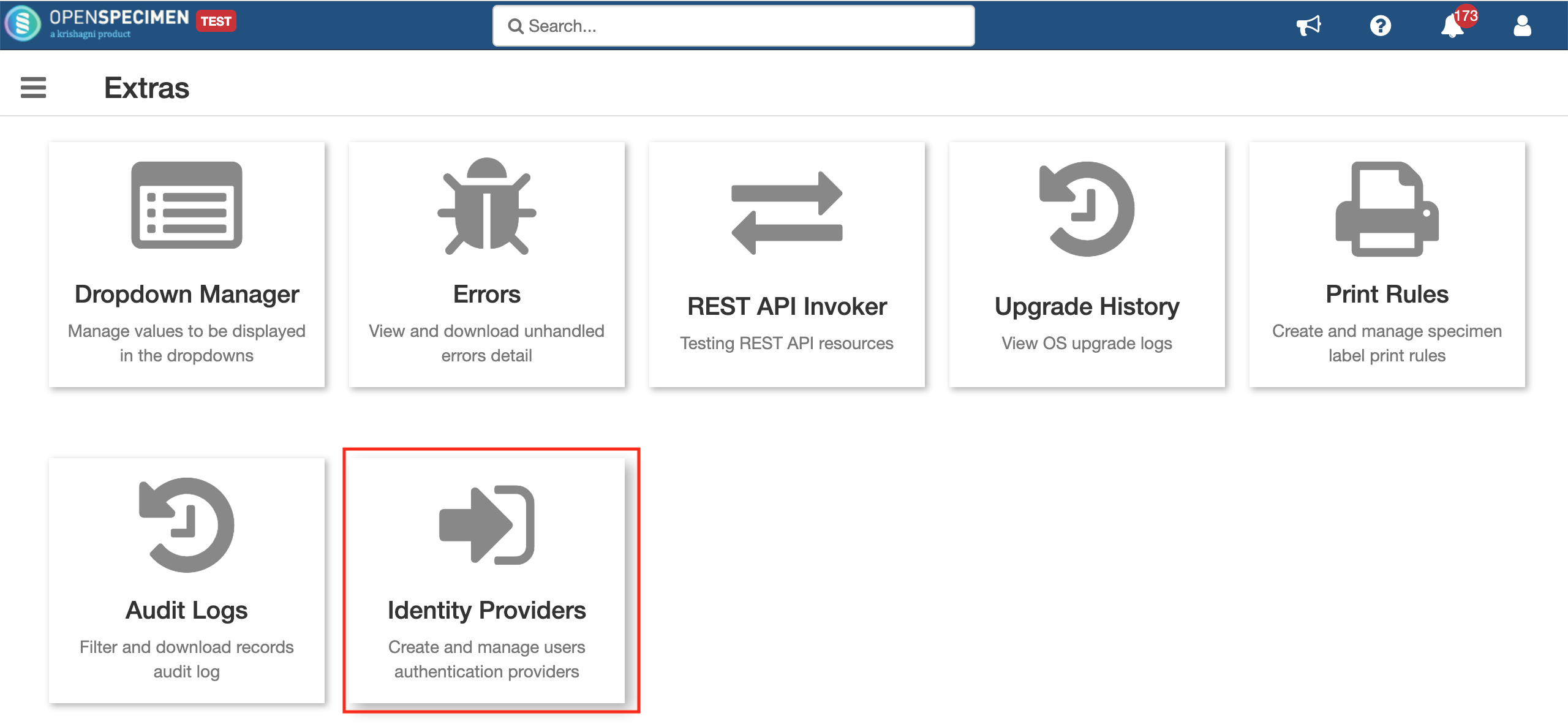
Super admins can configure LDAP via UI (v6.1 onwards) by going to Extras from the home page.
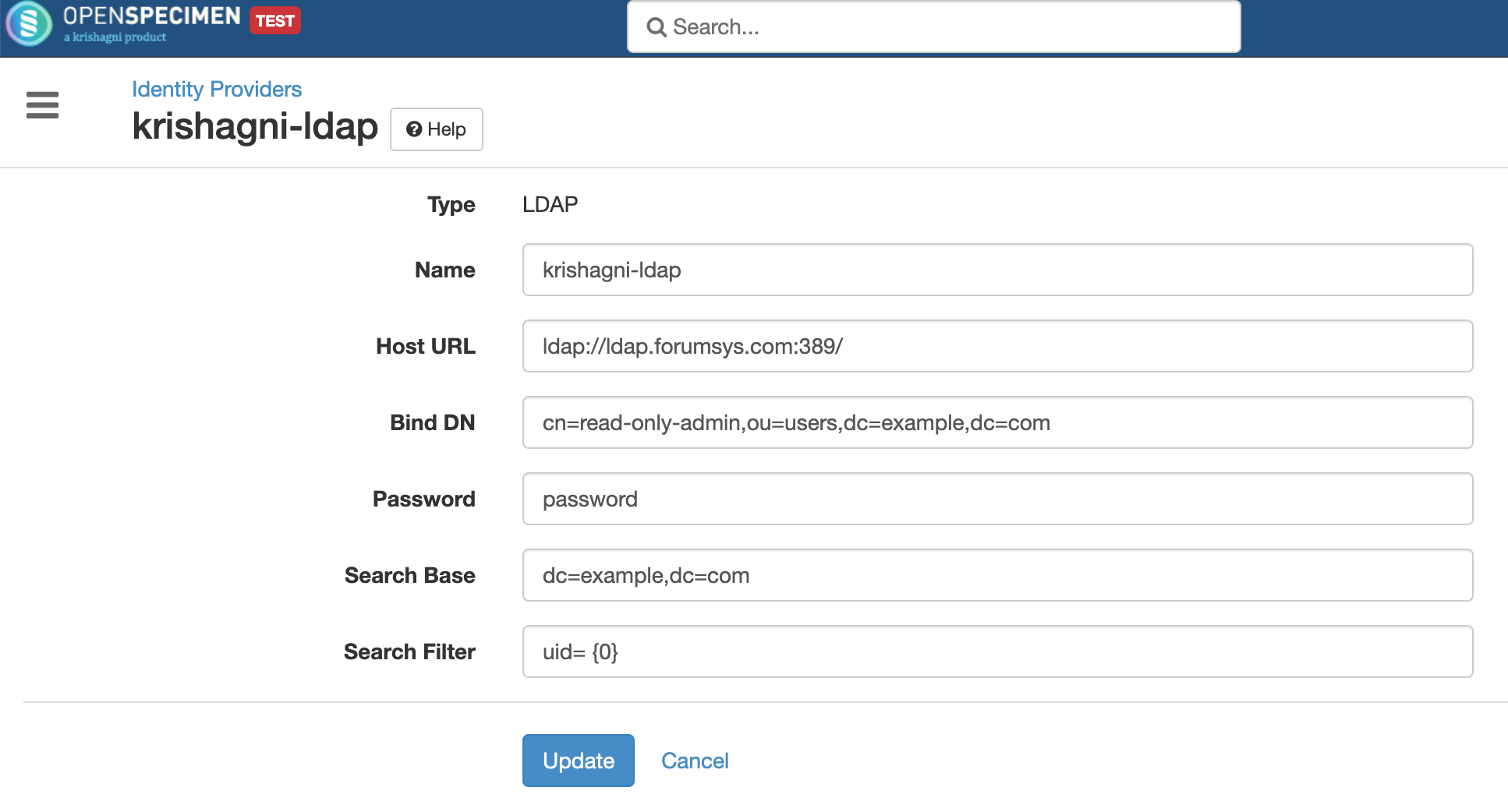
Click on 'Identity Providers' and create a new entry for registering to your LDAP. Select the type as LDAP and fill all required details
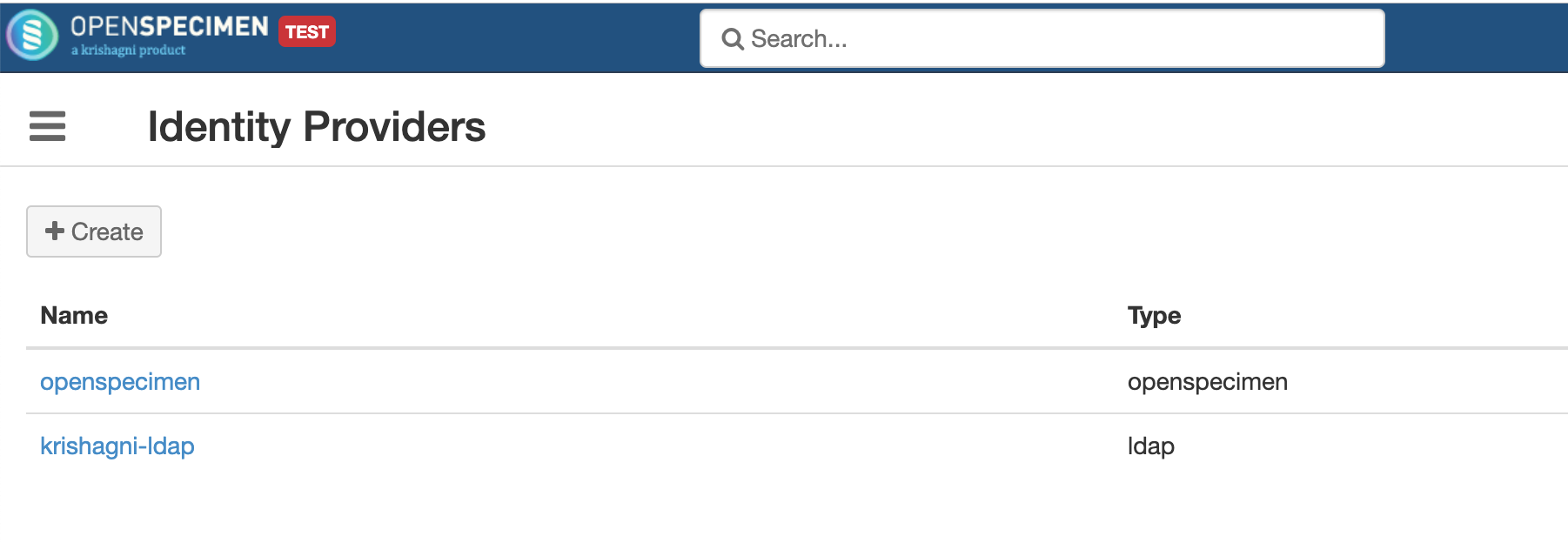
Once created, the list of all LDAPs registered are displayed and can be updated if required.
Via REST API
openspecimen/rest/ng/auth-domains
Use the register authentication domain resource for registering LDAP authentication domains in OpenSpecimen application. Use the HTTP POST method to call this API by passing the below details in JSON format.
Parameter | Details | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| name | A unique user-friendly name that end-user wants to give his/her domain. E.g., Hopkins_LDAP, KUMC_LDAP, etc. | |||||||||
| authType | Unique name for the LDAP. E.g., UNIV_LDAP, HOSP_LDAP. | |||||||||
| implClass | Should be "com.krishagni.catissueplus.core.auth.services.impl.LdapAuthenticationServiceImpl" If you are going to customize the LDAP implementation for some reason, replace the string with your custom class name. | |||||||||
| authProviderProps | This parameter is mandatory. There are two authentication strategies:
The parameter that comes under the authProviderProps parameter is described below. | |||||||||
url - LDAP URLs have the following syntax: ldap[s]://<hostname>:<port>/<base_dn>
| ||||||||||
userDnPatterns - User Dn pattern. Eg. "uid={0}" or in case of active directory "sAMAccountName={0}". OpenSpecimen creates full Dn using userDnPattern and baseDn and tries to authenticate by provided username and password. Eg. userName - "jonDoe",
password - "passwd"
url - ldap://ldap.forumsys.com:389/dc=example,dc=com
userDnPatterns - "uid={0}" or "sAMAccountName={0}"
Full Dn - "uid=jonDoe,dc=example,dc=com" or "sAMAccountName=jonDoe,dc=example,dc=com"
OR
url - ldap://ldap.forumsys.com:389/dc=example,dc=com
userDnPatterns - "uid={0}, ou=users" or "sAMAccountName={0},ou=users"
Full Dn - "uid=jonDoe, ou=users, dc=example, dc=com" or "sAMAccountName=jonDoe, ou=users, dc=example, dc=com"
| ||||||||||
| userDn - This is required for authenticating to the directory. Eg. "cn=read-only-admin,ou=users,dc=example,dc=com" | ||||||||||
| password - bind password | ||||||||||
| userSearchFilter - Search user using an attribute. Eg. "(uid={0})" or in case of active directory "(sAMAccountName={0})" | ||||||||||
userSearchBase - User search base, from where the search will be started. It might be an empty string like "" or "ou=People". If Oracle DBMS is used, then an empty string is treated as null, which will fail LDAP authentication. Therefore it is advised to specify the base node from which the search needs to be carried. Eg. Suppose users are resided in following directory:
1. ou=others,dc=example,dc=com
2. ou=users,dc=example,dc=com
3. ou=people,dc-example,dc=com
url - ldap://ldap.forumsys.com:389/dc=example,dc=com
userSearchFilter - "(uid={0})" or "(sAMAccountName={0})"
userSearchBase - ""
Search will start from "dc=example, dc=com", It will search user in all the sub directories.
OR
url - ldap://ldap.forumsys.com:389/dc=example,dc=com
userSearchFilter - "(uid={0})" or "(sAMAccountName={0})"
userSearchBase - "ou=people"
Search will start from "ou=people,dc=example,dc=com". It will search user only in ou=people.
|
http[s]:<host>:<port>/openspecimen/rest/ng/auth-domains
Use this URL to register the authentication domain in the OpenSpecimen application.
Result:
The response of this request will contain the details of the registered authentication domain.
Below is the example of the register authentication domain:
- Ldap Domain Registration :
| Method | POST: Use to register new domain PUT : Use to update existing domain |
| POST URL | openspecimen/rest/ng/auth-domains |
| PUT URL | openspecimen/rest/ng/auth-domains/{id} |
| Request | application/json |
| json | {
"name": "krishagni-ldap",
"implClass": "com.krishagni.catissueplus.core.auth.services.impl.LdapAuthenticationServiceImpl",
"authType": "ldap",
"authProviderProps": {
"url": "ldap://ldap.forumsys.com:389/",
"userDn": "cn=read-only-admin,ou=users,dc=example,dc=com",
"password": "passwd",
"userSearchFilter": "uid= {0}",
"userSearchBase": "dc=example,dc=com"
}
}
|
Response | {
"id": 3,
"name": "krishagni-ldap",
"implClass": "com.krishagni.catissueplus.core.auth.services.impl.LdapAuthenticationServiceImpl",
"authType": "ldap",
"authProviderProps": {
"url": "ldap://ldap.forumsys.com:389/",
"userDn": "cn=read-only-admin,ou=users,dc=example,dc=com",
"password": "passwd",
"userSearchFilter": "uid= {0}",
"userSearchBase": "dc=example,dc=com"
}
}
|
This section describes the response cases for register authentication API
code | Applies to | Status Message |
|---|---|---|
| 200 | All resources | Domain has been registered successfully |
| 400 | All requests | Invalid parameters, e.g. blank implClass in-case of a custom domain, duplicate domain name, etc |
| 401 | All requests | Authorization failed, the user doesn’t have the authority |
| 500 | All requests | Internal server error, encountered server error while performing operations or provided wrong LDAP information |
Debugging LDAP Issues
Run the below command on command prompt / terminal and fill the same details as configured on OpenSpecimen UI. This command will give you an error if there is an issue with configuration, and if it works fine, then the same configuration will work in OpenSpecimen.
ldapsearch -x -H <ldap_host> -b "<search_base>" -D "<bind_dn>" -W "objectclass=account"
For Example:
ldapsearch -x -D "cn=Manager,dc=krishagni,dc=in" -H ldap://192.168.121.133 -b "ou=People,dc=krishagni,dc=in" -W "uid=test"
The command will prompt for the password. Enter the same password that you entered in the password field on UI.
Here 'test' is the user account created in LDAP, and the same user needs to be created into OpenSpecimen. Here is a wiki page to setup LDAP users. (refer to via UI section)