To configure SAML, the system administrator has to do the following tasks:
...
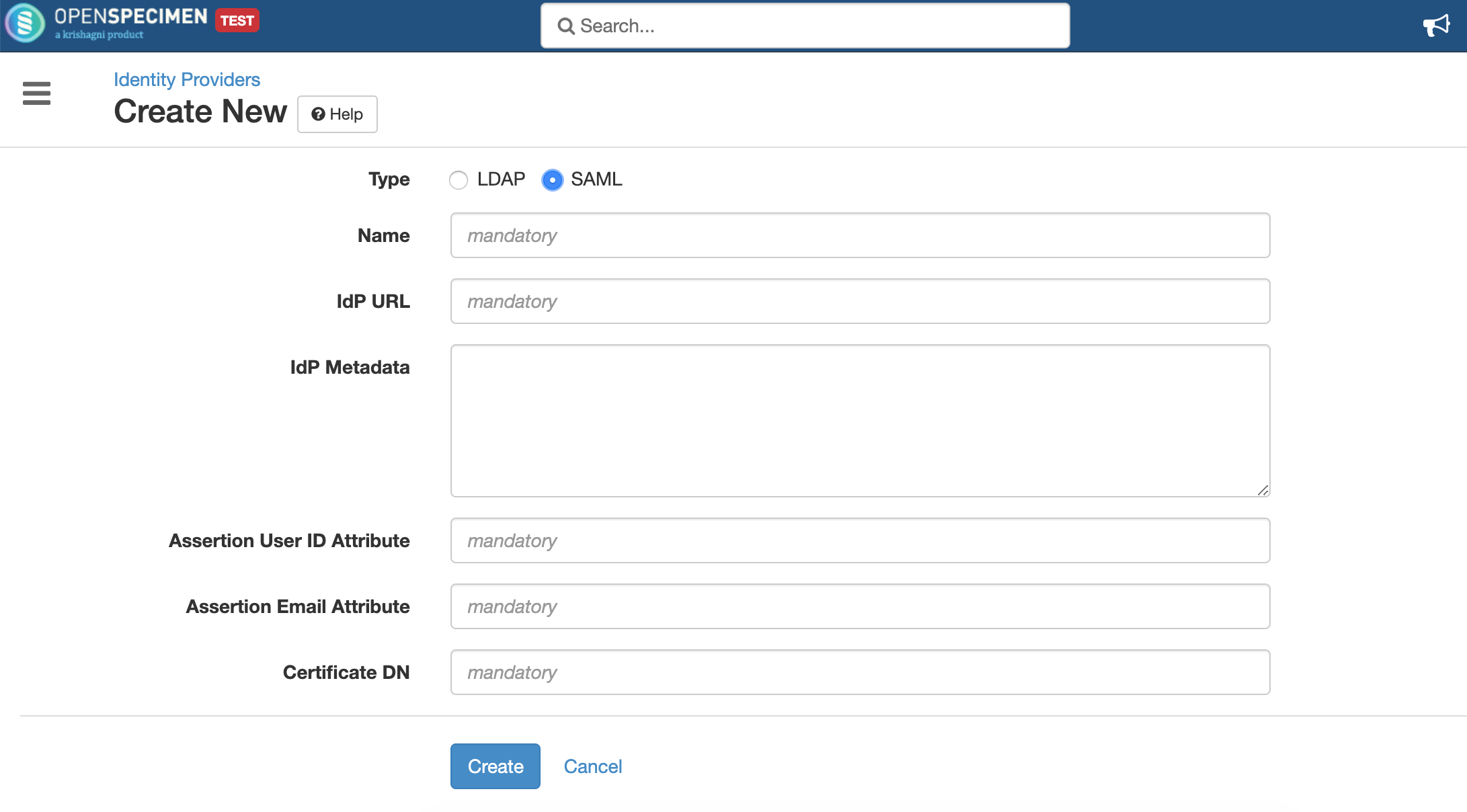
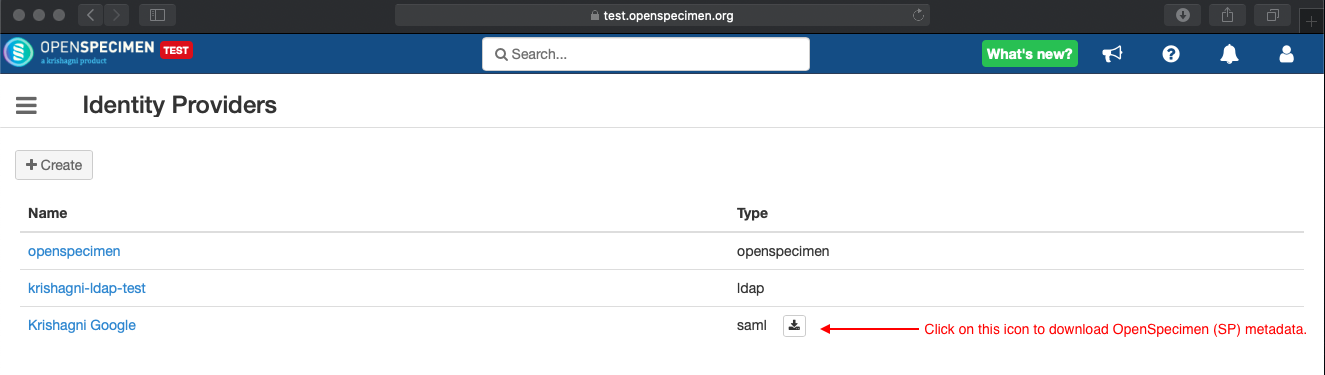
Click on 'Identity Providers' and create a new entry for registering to SAML. Select the type as SAML and fill all required details
Once SAML details are updated. Download the OpenSpecimen (Service Provider) metadata from the UI to register it into IdP server.
| Item | Description |
|---|---|
| Name | Unique name given to the identity provider or auth domain. This name appears in the sign-in dropdown. Selecting this option redirects users to the IdP page. |
| IdP URL | This is the value of entityID attribute present in the IdP metadata XML. |
| IdP Metadata | IdP metadata XML. This can be downloaded from the IdP server. OpenSpecimen uses this metadata for securely exchanging the messages with the IdP server. |
| User ID Attribute | The name of the attribute in the SAML assertion (received from the IdP server) that contains the user ID. Example uid, sAMAccountName etc. This is optional if the email attribute is specified (see below). The value of this attribute should match the login name of the OpenSpecimen user. |
| Email Attribute | The name of the attribute in the SAML assertion that contains the email address. This is optional if the user ID attribute is specified. |
| Certificate DN | This is used to generate the public & private keys for exchanging messages with the IdP server. The format of this field value is typically: cn=<Common Name>, ou=<Organisation Unit>, o=<Organisation>, c=<Country> Example: cn=demo.openspecimen.org,ou=Engineering,o=Krishagni,c=India Usually, OpenSpecimen instance hostname is used for the common name (cn) as in the above example. |
...